Risk Rating Methodology
Adapted from the Open Web Application Security Project (OWASP) Risk Rating Methodology.
Identify the assets
- Voter registration data
- Candidate registration data
- Voters list
- Voter ballot
- Polling station results
- Local jurisdiction results
- Regional jurisdiction results
- National results
Identify the actors
- Providers
- Electoral authority
- Observers
- Custody personnel
- Operators / field personnel / Poll workers
- General public
- Candidates / party representatives
- Voters
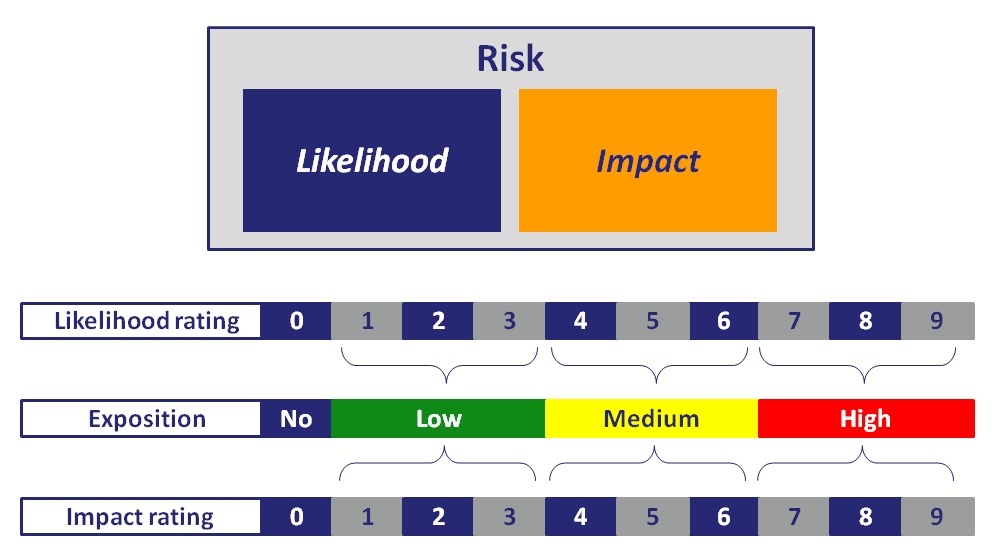
Likelihood Analysis
Threat Agent Factors
The first sets of factors are related to the threat agent involved. The goal here is to estimate the likelihood of a successful attack by this group of threat agents. Use the worst-case threat agent.
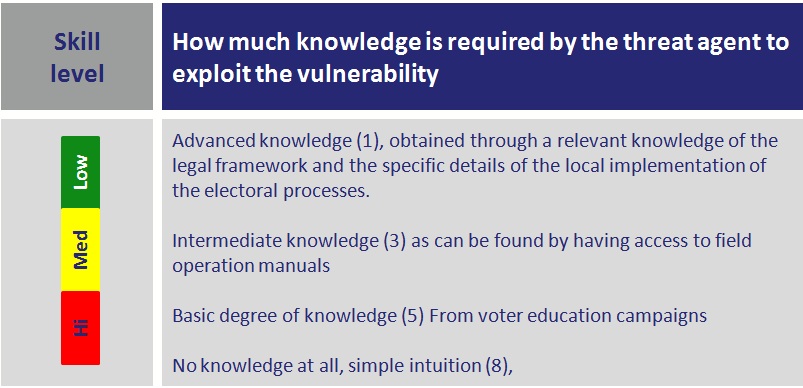
Skill level
How much knowledge of the electoral process is required by the group of threat agents?
Motivation
How motivated is this group of threat agents to find and exploit this vulnerability?
Resources
What resources are required for this group of threat agents to find and exploit this vulnerability?
Size
How large is this group of threat agents?
Vulnerability Factors
The next set of factors is related to the vulnerability involved. The goal here is to estimate the likelihood of the particular vulnerability being discovered and exploited. Assume the threat agent selected above.
Ease of exploit
How easy is it for this group of threat agents to actually exploit this vulnerability?
Accountability
Are the threat agents’ actions traceable to an individual?
Impact Analysis
Scope
The impact of a given electoral vulnerability depends on its scope of action, or likewise, in how relevant is the potential change to the election outcome.
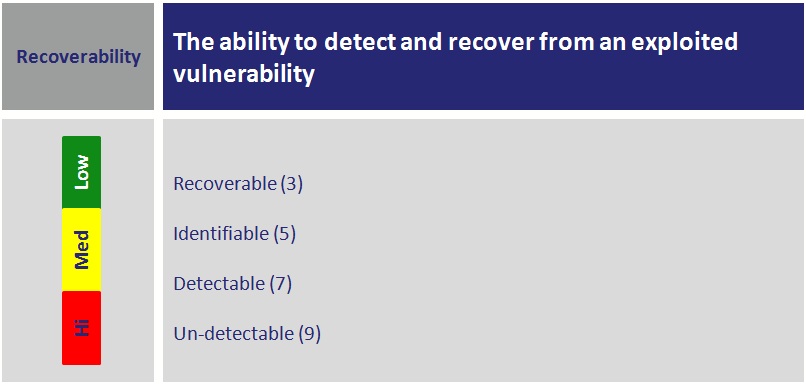
Recoverability
The ability to detect and recover from an exploited vulnerability is an important component of the Impact analysis. As such there are different levels of detection and recovery
Final rating
After these ratings are completed, an overall number for impact and another for likelihood is produced by calculating an average for both, the likelihood and impact ratings. The methodology refers to these as follows:
lj: average rating of likehood for vulnerability j
ij: average rating of impact for vulnerability j